Information security is critical for organizations of all sizes, with high stakes. For example, a data breach or a cyber-attack can result in loss of revenue, reputation damage, and even legal liability. That’s why it’s crucial to have a comprehensive Information Security Program, including well-written policies, standards, and procedures. These documents provide a roadmap for your organization to follow, ensuring that your sensitive information is protected and that your employees know their roles and responsibilities regarding information security.
Developing these documents can seem daunting, especially if you need a clear framework. That’s where this blog post comes in. We’ll introduce you to a pyramid approach to policy documentation that corporate IT departments have successfully used. This approach involves creating separate documents for each policy, standard, and procedure for a specific topic, allowing you to manage your documentation and reduce approval time efficiently. By the end of this blog post, you’ll better understand how to develop well-written policies, standards, and procedures that will help you protect your organization’s sensitive information.
The Pyramid Approach
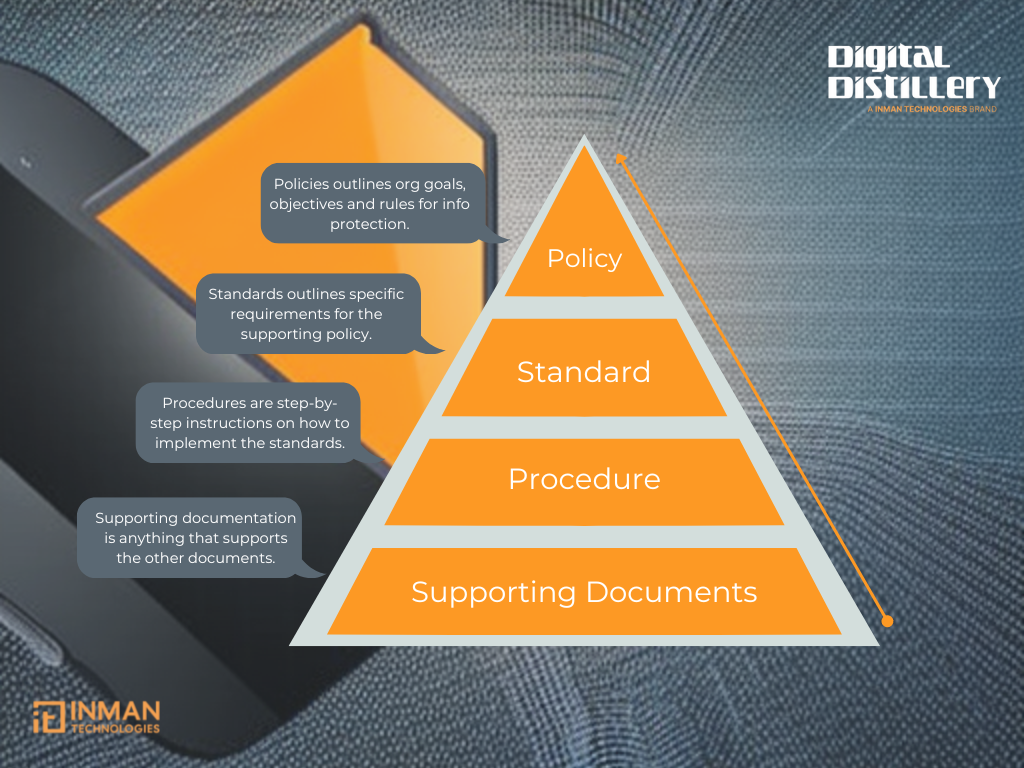
There are many ways to approach information security policy documentation, but we’ve found that the pyramid approach is the most effective. This approach involves creating separate documents for each policy, standard, and procedure for a specific topic.
Let’s use the example of a password policy to illustrate this approach. At the top of the pyramid is the policy. This document provides the overall policy statement that gives the “marching orders” to your users. For example, in the case of the password policy, a policy statement might be “Passwords must be complex.”
Next, we have the Standards document, which provides the technical details to support the policy. In our example, the standards might be “Passwords must be eight characters long and contain upper case, lower case, number, and symbol.”
After the Standards, we have the Procedures document. This document provides step-by-step instructions for users to follow. For example, a procedure document for the password policy might be “Changing Passwords.”
Finally, we have Supporting documentation. These documents are forms or checklists that may only be necessary for some topics but could be helpful for users who are required to follow these documents.
Benefits of the Pyramid Approach
At first, the pyramid approach will quadruple your documentation. However, once you get started, it makes managing documentation more efficient. For example, if you document everything in one extensive document, you’ll need to approve that entire document again if you make changes to just one item. The approval process can be lengthy and frustrating, especially if many need to approve the document. However, if you have separate documents for each policy, standard, and procedure, you’ll only need to approve the specific document for updates.
Using the example of the password policy, you might have the following documents:
- Password Policy – CIO or Sr. Management approval depends on the organization
- Password Standards – Sr. Management approval, depending on the organization
- Password Procedures – Department Manager or Team Lead approval, depending on the organization
Corporate IT departments have successfully used this framework to develop their IT policies, standards, and procedures. In the following article, we’ll talk about document management. If you have any comments or questions, please leave a comment below.
The pyramid approach can help you develop well-written policies, standards, and procedures for your Information Security Program. By following this framework, you can efficiently manage your documentation, reduce approval time, and protect your organization’s sensitive information.