Making IT Make Sense
Fort Worth Outsourced IT Support & IT Services
Let our team at Inman Technologies provide you with the best IT support and solutions to increase your profitability and allow you to focus on growing your business.
Your Neighborhood IT Department
Why Choose Us
We Listen
We take a genuine approach to best understand your business by listening to your needs and simplifying the entire experience.
We Discover
We do a deeper dive into your current processes, network, and infrastructure to identify strengths, weaknesses, and overall IT needs.
We Recommend
We take our findings from the assessments and recommend an IT approach that will best support your business needs and goals.
We Improve
We keep your technology environment constantly improving as needed to help you maintain a competitive edge in your industry.
Client Success Stories

"I have had the good fortune to work with Inman Technologies for the past two years where they have managed and supported a full range of IT services from basic computer setup and software management to a complete overhaul or our servers and security protocols.
Above all, we have developed a relationship with Sean and his team due to their thoroughness and quick response to all our needs."
Bobby Snyder, President of Construction
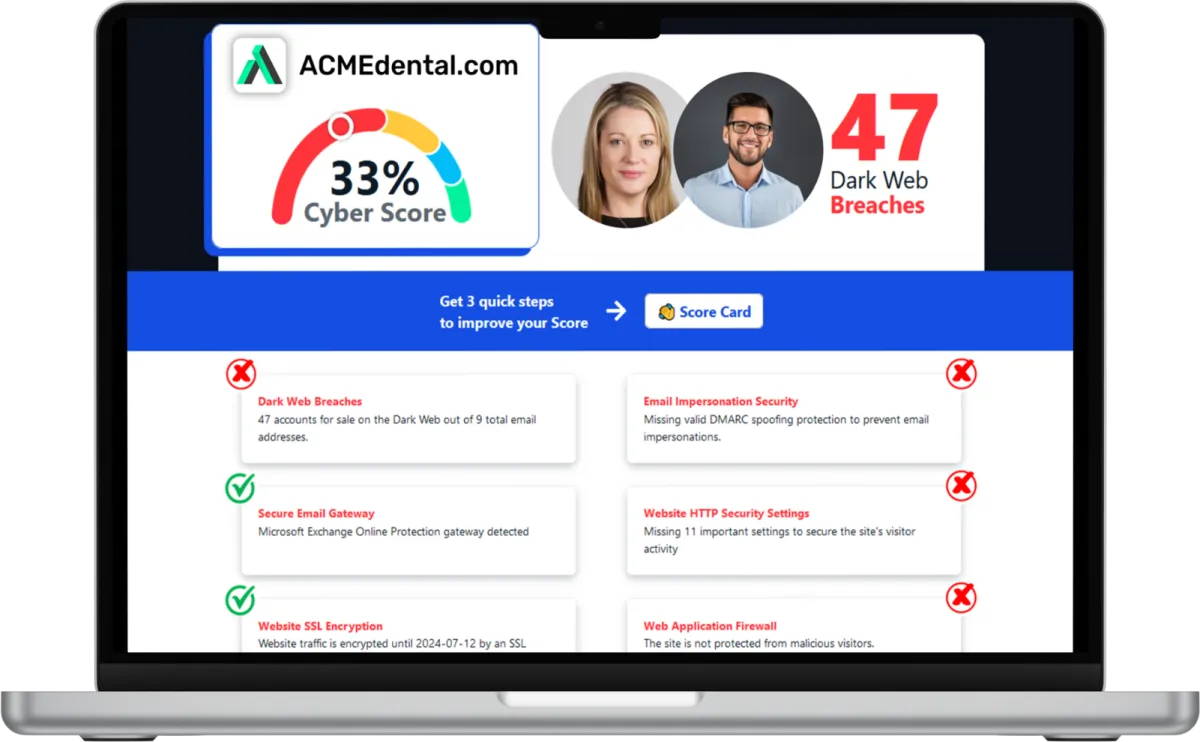
Want to see your Score? Get it in 30 seconds!
If You’ve Been Dealing with IT Challenges,
You’re Not Alone

Sean Inman
Founder & CEO
Inman Technologies is Here to Help.
Inman Technologies is a leading managed IT service provider in Fort Worth, TX, offering a comprehensive selection of outsourced IT support and IT services to businesses in Fort Worth, TX, and the surrounding areas, including Aledo, Willow Park, Hudson Oaks, and Weatherford, TX, and Oklahoma City and Edmond, OK. We specialize in providing IT support and Cybersecurity services to meet the unique needs of businesses.
Call 682-882-6348 today for comprehensive cybersecurity and managed IT services tailored to your needs.
Schedule an Appointment Today
Our Services
We monitor, maintain and manage your IT systems around-the-clock so you can focus on growing your business.
We provide robust protection against cyber threats, ensuring the confidentiality, integrity and availability of your data.
We offer assistance with any sort of IT project - ensuring it's completed on time and on budget.
Harness the Power of AI for Your Business
At Inman Technologies, we bring cutting-edge AI solutions to businesses of all sizes. Our AI as a Service offerings are designed to simplify your operations, enhance customer experiences, and drive measurable growth. From automating customer interactions to optimizing your marketing strategies, we deliver secure, tailored AI tools that make your business smarter and more efficient.
What Clients Say About Us
Partners and products we support to deliver unparalleled productivity:







Business Technology Insights
Explore expert insights, trends, and expert advice on the ever-evolving landscape of information technology. Dive in to discover how we leverage cutting-edge solutions to empower businesses and drive innovation.

9 Signs That Your Smart Home Device Has Been Hacked
Smart home devices are becoming more popular and convenient. But they also pose some serious security risks.

5 Cybersecurity Predictions for 2024 You Should Plan For
Cybersecurity is a constantly evolving field. There are new threats, technologies, and opportunities emerging every year.

Workspaces, a VPN & More – Learn the Newest Microsoft ...
Microsoft Edge continues to redefine user experiences. This is due to Microsoft’s commitment to innovation.

Cyber Insurance: What Fort Worth Businesses Need to Know
In today’s ever‑evolving cyber threat landscape, even the most well‑protected firms in Fort Worth, and surrounding communities are vulnerable. Small and mid‑sized businesses increasingly face ransomware, data breaches, and social engineering attacks, yet many assume their standard policies fully protect them. In most cases, they don’t.
According to a 2023 report by IBM, 43% of cyberattacks target small and mid‑sized businesses, and the average breach cost has climbed to $2.98 million. That kind of loss can devastate local companies.
What Cyber Insurance Typically Covers
First‑Party Coverage
These are costs your business directly incurs as a result of a cyber event.
Breach Response: This includes the cost of forensic investigations to determine what data was compromised, legal guidance on compliance requirements, customer notification efforts, and credit monitoring for affected individuals. These services are often mandated by laws like the Texas Identity Theft Enforcement and Protection Act.
Business Interruption: Covers lost revenue due to system downtime caused by a cyber incident. For example, if your business is offline for five days due to a ransomware attack, this coverage compensates you for the revenue you would’ve earned during that period—provided you can document losses.
Ransomware & Cyber Extortion: Pays the ransom demands (if necessary), legal consultation on whether to pay, and professional negotiators. It also covers costs of decryption tools and restoration services—especially critical as ransomware-as-a-service (RaaS) groups like LockBit target small U.S. businesses.
Data Restoration: Covers the cost of recovering corrupted or encrypted data. This often involves data recovery specialists and could include rebuilding entire databases or software systems.
Reputation Management: Provides access to crisis PR firms that help manage your company’s public image following a breach. This might include press releases, media coordination, and online reputation repair.
Third‑Party Liability
These costs arise when others hold your business responsible for a cyber incident.
Privacy Liability: Covers legal costs if customer or employee data is stolen or exposed. This includes defense against lawsuits and regulatory investigations, particularly from HIPAA or GDPR regulators.
Media Liability: Protects against defamation, copyright infringement, or intellectual property violations arising from your online content—critical if your website or social media accounts are compromised and publish unauthorized material.
Legal Defense & Settlements: Pays attorney fees, court costs, and settlement amounts tied to covered incidents. For example, if you’re sued by a vendor whose data was compromised through your network, this clause activates.
Regulatory Fines: Some policies offer limited coverage for fines and penalties assessed by regulatory bodies like the FTC or HHS, though coverage often depends on whether the fine is insurable under state law.
What Isn’t Covered
Negligence or Poor Cyber Hygiene
If you fail to implement fundamental protections like multi-factor authentication (MFA), endpoint detection, or timely software patching, insurers may deny your claim. Most policies now require businesses to attest to a minimum level of cyber hygiene.
Pre‑Existing or Ongoing Incidents
If you purchase a policy after you’ve already discovered suspicious activity—or knew you had vulnerabilities and didn’t address them—those events likely won’t be covered.
State‑Sponsored or War‑Related Attacks
Many policies include a “war exclusion” clause, which can void coverage for attacks attributed to nation-states. This has caused issues with ransomware attacks like NotPetya, where attribution is murky. Some insurers now offer riders for nation-state attribution coverage.
Insider Threats
Most policies do not automatically cover malicious acts by employees unless a specific endorsement is included. This includes theft of data, fraud, or sabotage by current or former staff.
Reputational Damage & Future Lost Revenue
While some policies include crisis communication support, they typically don’t reimburse for long-term losses like loss of customer trust, brand value, or market share.
Social Engineering Fraud
Phishing attacks, invoice fraud, and executive impersonation scams (BEC) are rarely covered under standard policies. Separate “social engineering fraud” riders are often needed—and typically only pay out if strict verification protocols were followed.
Physical Hardware Upgrades
Cyber insurance won’t pay for post-breach hardware upgrades—such as replacing old firewalls, routers, or workstations—unless damage was physically caused by the attack, which is rare.
Choosing the Right Policy
Here’s how Fort Worth businesses can ensure better coverage:
Balance Cyber Hygiene with Coverage
Conduct regular risk assessments and meet common insurer requirements like endpoint protection, encryption, and MFA. Consider CMMC or CIS Controls as baseline frameworks.
Enrich Your Policy with Riders
Add-ons for social engineering, dependent systems failures, and cloud data breaches help fill dangerous gaps.
Clarify War & State‑Sponsor Exclusions
Ask your broker: “Is there coverage if attribution to a nation-state cannot be confirmed?” Some policies are now offering conditional coverage.
Match Coverage to Local Risk
Construction, legal, and healthcare firms in Texas often hold sensitive data. Ensure your liability limits reflect your regulatory exposure and contractual obligations.
Prepare for Claims Ahead of Time
Create a cyber incident response plan, document it, and test it annually. Insurers expect a defined process, designated response team, and third-party partners in place before a breach occurs.
How Inman Technologies Supports Your Cyber & Insurance Strategy
We provide Fort Worth-area businesses with:
Cybersecurity Hardening: 24/7 endpoint protection, firewall management, vulnerability scanning, and Microsoft 365 security best practices implementation.
Risk Assessment & Policy Alignment: We evaluate your current environment, help you meet insurer requirements, and guide your broker conversations to avoid costly exclusions.
Incident Readiness: From playbooks to vendor coordination (legal, forensic, PR), we help you meet time-sensitive policy reporting requirements.
Insurance Vendor Partnerships: Through our network, we can introduce you to providers offering comprehensive and transparent cyber insurance tailored to small businesses.
Final Thought
Cyber insurance isn’t just a financial safety net—it’s a business resilience strategy. But policies only work when they’re built on top of proactive cybersecurity practices.
If you’re a business owner in Fort Worth or nearby communities and aren’t sure what your policy really covers, let’s talk.
📞 Book a free cyber risk review with Inman Technologies today—and bring peace of mind to your policy.
Frequently Asked Questions
What are the benefits of cybersecurity services?
Cybersecurity services offer numerous advantages for businesses. They protect your sensitive data from unauthorized access, safeguard your systems from cyber threats, ensure compliance with industry regulations, and enhance the overall resilience of your IT infrastructure.
What are managed IT service providers?
Managed IT service providers handle your IT needs, allowing you to focus on your core business operations. They provide proactive IT support, network monitoring, data backup, cybersecurity, and other essential services to ensure the smooth functioning of your IT environment.
What are IT security services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include but are not limited to network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
What makes our IT Support different from other MSPs?
At Inman Technologies, we stand out as a premier outsourced IT support provider in Fort Worth through our unique approach to technology services. Unlike other providers, we don't believe in one-size-fits-all solutions or long-term contracts that lock you in. Instead, we offer:
✔️ Flexible Service Model
✔️ Comprehensive Support
✔️ Innovation Focus - AI-powered solutions
✔️ Local Expertise
Whether you're a small tax office or a growing enterprise, our outsourced IT support services provide the flexibility, expertise, and personal attention your business needs to thrive in today's digital landscape.
📅 Schedule an Appointment With Us to learn more about our unique approach to IT support.
Share Your IT Burdens With Us
Spend less time on IT problems and more time growing your business. Let’s get to know each other and determine how our partnership could grow. With us on your side, develop customized security plans, stronger communication strategies, and a better plan for the future.
Click the button below to schedule your appointment. We’re ready to jumpstart your IT journey.












