Business Outcomes Powered by IT
Fort Worth Outsourced IT Support & IT Services
Let our team at Inman Technologies provide you with the best IT support and solutions to increase your profitability and allow you to focus on growing your business.
Your Neighborhood IT Department
Why Choose Us
We Listen
We take a genuine approach to best understand your business by listening to your needs and simplifying the entire experience.
We Discover
We do a deeper dive into your current processes, network, and infrastructure to identify strengths, weaknesses, and overall IT needs.
We Recommend
We take our findings from the assessments and recommend an IT approach that will best support your business needs and goals.
We Improve
We keep your technology environment constantly improving as needed to help you maintain a competitive edge in your industry.
Client Success Stories

"I have had the good fortune to work with Inman Technologies for the past two years where they have managed and supported a full range of IT services from basic computer setup and software management to a complete overhaul or our servers and security protocols.
Above all, we have developed a relationship with Sean and his team due to their thoroughness and quick response to all our needs."
Bobby Snyder, President of Construction
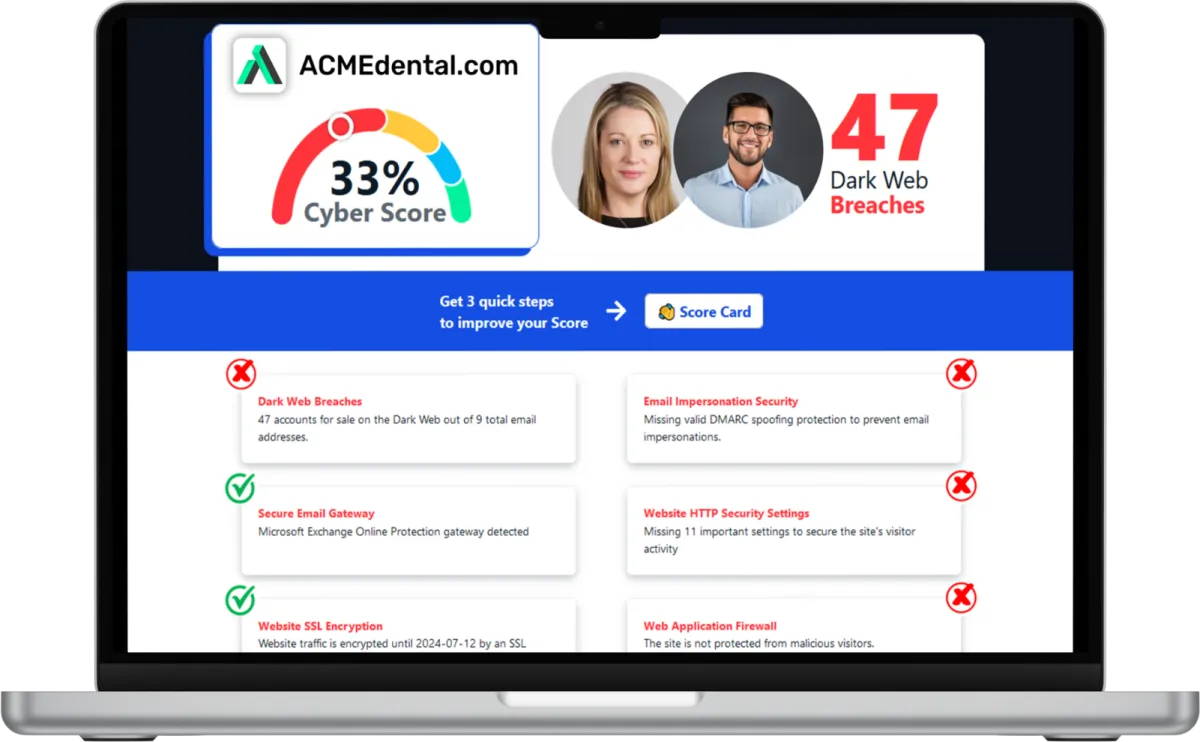
Want to see your Score? Get it in 30 seconds!
If You’ve Been Dealing with IT Challenges,
You’re Not Alone

Sean Inman
Founder & CEO
Inman Technologies is Here to Help.
Inman Technologies is a leading managed IT service provider in Fort Worth, TX, offering a comprehensive selection of outsourced IT support and IT services to businesses in Fort Worth, TX, and the surrounding areas, including Aledo, Willow Park, Hudson Oaks, and Weatherford, TX, and Oklahoma City and Edmond, OK. We specialize in providing IT support and Cybersecurity services to meet the unique needs of businesses.
Call 682-882-9344 today for comprehensive cybersecurity and managed IT services tailored to your needs.
Schedule an Appointment Today
Our Services
We monitor, maintain and manage your IT systems around-the-clock so you can focus on growing your business.
We provide robust protection against cyber threats, ensuring the confidentiality, integrity and availability of your data.
We offer assistance with any sort of IT project - ensuring it's completed on time and on budget.
Harness the Power of AI for Your Business
At Inman Technologies, we bring cutting-edge AI solutions to businesses of all sizes. Our AI as a Service offerings are designed to simplify your operations, enhance customer experiences, and drive measurable growth. From automating customer interactions to optimizing your marketing strategies, we deliver secure, tailored AI tools that make your business smarter and more efficient.
What Clients Say About Us
Partners and products we support to deliver unparalleled productivity:
Business Technology Insights
Explore expert insights, trends, and expert advice on the ever-evolving landscape of information technology. Dive in to discover how we leverage cutting-edge solutions to empower businesses and drive innovation.

9 Signs That Your Smart Home Device Has Been Hacked
Smart home devices are becoming more popular and convenient. But they also pose some serious security risks.

5 Cybersecurity Predictions for 2024 You Should Plan For
Cybersecurity is a constantly evolving field. There are new threats, technologies, and opportunities emerging every year.

Workspaces, a VPN & More – Learn the Newest Microsoft ...
Microsoft Edge continues to redefine user experiences. This is due to Microsoft’s commitment to innovation.

Passkeys: The Future of Logging In Without Passwords
We’ve all been there, typing passwords we can barely remember, struggling to reset them, or worrying about their security. Passwords are the foundation of many of our digital lives, but they come with a lot of risks. Enter passkeys, a new way of logging in that promises to make passwords a thing of the past.
Let’s break down what passkeys are, how they work, and why they might just be better than the passwords we use every day.
What is a Passkey?
A passkey is a new way to log into websites or apps without typing a password. Instead of remembering a long string of characters, passkeys use a pair of keys:
A private key, which is stored securely on your device (like your phone or computer).
A public key, which is stored on the website or app you’re logging into.
When you want to sign in, your device proves it has the private key (without actually sending it to the website). No password to type, no password to steal, and no password to phish.
For more on how passkeys work with public key cryptography, visit WebAuthn - Mozilla Developer Network and FIDO Alliance.
How Do Passkeys Work?
Let’s simplify how passkeys work in two steps:
1) You create a passkey
When you sign up or log in to a site (say your email), your device creates a unique passkey for that site. The website stores the public key, and your device keeps the private key. Think of it as creating a secret handshake between your device and the website.
2) You sign in
Next time you want to log in:
The website sends a “challenge” to your device.
Your device uses the private key to sign the challenge.
The website checks the signature with the public key it already has.
To unlock the private key, your device asks for something you can easily do, like Face ID, Touch ID, or a PIN. Your biometric data (like your face or fingerprint) never leaves your device—it just unlocks the private key.
For more on how passkeys work under the hood, check out Apple’s explanation on passkeys and Google’s support page for Passkeys.
Passkeys vs. Passwords: What’s the Difference?
Passwords: The Old Way
Passwords are shared secrets—something you and the website both know. But there are problems:
Phishing: You might type your password into a fake site.
Reusing passwords: People often use the same password across multiple sites, making them an easy target for hackers.
Data breaches: If a website’s database is hacked, attackers can get your password.
Human behavior: People pick easy-to-guess passwords or reuse them, which makes it easier for hackers to guess.
Passkeys: The New Way
No shared secrets: Passkeys are unique to each website. There’s nothing to steal or share.
No password to remember or type: The passkey is stored securely on your device, making it harder to phish or reuse.
Stronger security: Even if a website is breached, attackers only get the public key—not the private key—so they can’t log in as you.
For more on the risks of passwords, visit Cybersecurity & Infrastructure Security Agency (CISA) on Password Security and Verizon’s 2021 Data Breach Investigations Report.
Why Are Passkeys Better Than Passwords?
Better protection against phishing
Passkeys won’t let you log into a fake website, even if the site tries to trick you. With passwords, you might not realize the website is fake.No more password reuse
Each passkey is unique to one website, so even if one account is compromised, hackers can’t use it to break into your other accounts.Safer if websites are breached
If a website is hacked, attackers only get the public key, which can’t be used to log in. Password databases, on the other hand, are valuable targets for hackers because passwords can be cracked or reused.Simpler and easier to use
With passkeys, you don’t have to remember, type, or reset passwords. You simply unlock your device with your fingerprint or face, and you’re in.
The Honest Truth: Passkeys Aren’t Perfect
While passkeys are a big improvement, they’re not foolproof. Here are some things to keep in mind:
If your device is compromised, passkeys can’t protect you
Passkeys protect your login, but they can’t stop malware or other attacks that target your device.Account recovery can be tricky
If you lose your device or need to recover your account, how easy it is to regain access depends on the service. If they use weak recovery methods, like SMS, attackers could still get in.Syncing passkeys introduces new risks
If your passkeys are synced across devices (like in iCloud or Google’s cloud), a hacker who compromises your cloud account could gain access to your passkeys. So, securing your cloud account is crucial.Not all sites support passkeys
Some older apps and websites still rely on passwords, so you may run into trouble if you try to use passkeys everywhere just yet.
For a deeper dive into security risks, check out CISA’s multi-factor authentication guidance.
Are Passkeys Better Than Passwords?
For most people, yes—passkeys offer a safer, simpler way to log in, especially for common services like email and social media. But they're not a silver bullet.
Passkeys remove most of the problems with passwords (phishing, password reuse, database breaches), but they don’t cover everything. They work best when combined with other security measures.
What You Can Do Right Now
For Individuals:
Enable passkeys wherever you can (email, password manager, banking apps, etc.).
Lock down your device accounts (Apple ID, Google Account, etc.) with strong multi-factor authentication (MFA).
Use a backup sign-in method that’s also secure—avoid relying on SMS for recovery.
For Businesses:
Start using passkeys for your employees, especially for admins, IT staff, and anyone who accesses sensitive data.
Use stronger MFA for accounts that don’t yet support passkeys.
Have a plan for account recovery that doesn’t rely on weak methods like SMS.
Educate your team about passkeys and how they work.
FAQ
“Are passkeys the same as Face ID or Touch ID?”
No. Face ID and Touch ID are just ways to unlock the private key stored on your device. The passkey itself is a cryptographic key that helps you sign in securely.
“What happens if a website is hacked? Can they steal my passkey?”
No, the attackers would only get the public key, which can’t be used to log in. Your private key stays secure on your device.
“What if I lose my phone?”
If your passkeys are synced to your cloud account, you can recover them on a new device. But you’ll need to make sure your account recovery methods are secure.
“Do passkeys replace multi-factor authentication (MFA)?”
In many cases, yes—passkeys are already a type of MFA because they require something you have (your device) and something you can do (biometrics). But for high-risk accounts, additional steps may still be needed.
Bottom Line
Passwords are becoming outdated. Passkeys offer a much safer, simpler way to log in—and they’re harder to steal or misuse. While they’re not perfect, they’re a big step forward in securing your digital life. Start using passkeys wherever you can, and make sure you have strong recovery options in place to keep your accounts safe.
Frequently Asked Questions
What are the benefits of cybersecurity services?
Cybersecurity services offer numerous advantages for businesses. They protect your sensitive data from unauthorized access, safeguard your systems from cyber threats, ensure compliance with industry regulations, and enhance the overall resilience of your IT infrastructure.
What are managed IT service providers?
Managed IT service providers handle your IT needs, allowing you to focus on your core business operations. They provide proactive IT support, network monitoring, data backup, cybersecurity, and other essential services to ensure the smooth functioning of your IT environment.
What are IT security services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include but are not limited to network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
What makes our IT Support different from other MSPs?
At Inman Technologies, we stand out as a premier outsourced IT support provider in Fort Worth through our unique approach to technology services. Unlike other providers, we don't believe in one-size-fits-all solutions or long-term contracts that lock you in. Instead, we offer:
✔️ Flexible Service Model
✔️ Comprehensive Support
✔️ Innovation Focus - AI-powered solutions
✔️ Local Expertise
Whether you're a small tax office or a growing enterprise, our outsourced IT support services provide the flexibility, expertise, and personal attention your business needs to thrive in today's digital landscape.
📅 Schedule an Appointment With Us to learn more about our unique approach to IT support.
Share Your IT Burdens With Us
Spend less time on IT problems and more time growing your business. Let’s get to know each other and determine how our partnership could grow. With us on your side, develop customized security plans, stronger communication strategies, and a better plan for the future.
Click the button below to schedule your appointment. We’re ready to jumpstart your IT journey.
























