Making IT Make Sense
Fort Worth Outsourced IT Support & IT Services
Let our team at Inman Technologies provide you with the best IT support and solutions to increase your profitability and allow you to focus on growing your business.
Your Neighborhood IT Department
Why Choose Us
We Listen
We take a genuine approach to best understand your business by listening to your needs and simplifying the entire experience.
We Discover
We do a deeper dive into your current processes, network, and infrastructure to identify strengths, weaknesses, and overall IT needs.
We Recommend
We take our findings from the assessments and recommend an IT approach that will best support your business needs and goals.
We Improve
We keep your technology environment constantly improving as needed to help you maintain a competitive edge in your industry.
Client Success Stories

"I have had the good fortune to work with Inman Technologies for the past two years where they have managed and supported a full range of IT services from basic computer setup and software management to a complete overhaul or our servers and security protocols.
Above all, we have developed a relationship with Sean and his team due to their thoroughness and quick response to all our needs."
Bobby Snyder, President of Construction
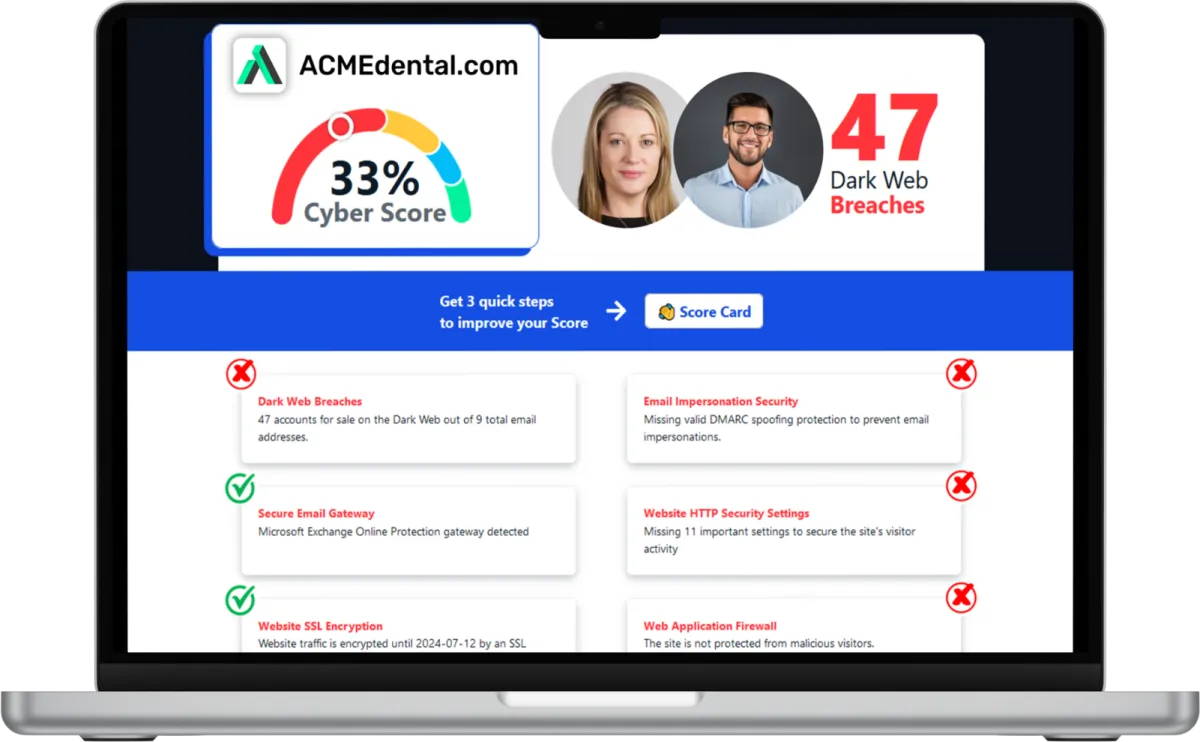
Want to see your Score? Get it in 30 seconds!
If You’ve Been Dealing with IT Challenges,
You’re Not Alone

Sean Inman
Founder & CEO
Inman Technologies is Here to Help.
Inman Technologies is a leading managed IT service provider in Fort Worth, TX, offering a comprehensive selection of outsourced IT support and IT services to businesses in Fort Worth, TX, and the surrounding areas, including Aledo, Willow Park, Hudson Oaks, and Weatherford, TX, and Oklahoma City and Edmond, OK. We specialize in providing IT support and Cybersecurity services to meet the unique needs of businesses.
Call 682-882-3001 today for comprehensive cybersecurity and managed IT services tailored to your needs.
Schedule an Appointment Today
Our Services
We monitor, maintain and manage your IT systems around-the-clock so you can focus on growing your business.
We provide robust protection against cyber threats, ensuring the confidentiality, integrity and availability of your data.
We offer assistance with any sort of IT project - ensuring it's completed on time and on budget.
Harness the Power of AI for Your Business
At Inman Technologies, we bring cutting-edge AI solutions to businesses of all sizes. Our AI as a Service offerings are designed to simplify your operations, enhance customer experiences, and drive measurable growth. From automating customer interactions to optimizing your marketing strategies, we deliver secure, tailored AI tools that make your business smarter and more efficient.
What Clients Say About Us
Partners and products we support to deliver unparalleled productivity:







Business Technology Insights
Explore expert insights, trends, and expert advice on the ever-evolving landscape of information technology. Dive in to discover how we leverage cutting-edge solutions to empower businesses and drive innovation.

9 Signs That Your Smart Home Device Has Been Hacked
Smart home devices are becoming more popular and convenient. But they also pose some serious security risks.

5 Cybersecurity Predictions for 2024 You Should Plan For
Cybersecurity is a constantly evolving field. There are new threats, technologies, and opportunities emerging every year.

Workspaces, a VPN & More – Learn the Newest Microsoft ...
Microsoft Edge continues to redefine user experiences. This is due to Microsoft’s commitment to innovation.

Phishing 2.0: How AI is Amplifying the Danger and What You Can Do
Phishing has always posed a significant threat, but now with AI in the mix, it's more dangerous than ever. Welcome to Phishing 2.0 - it's smarter, more convincing, and harder to detect. Understanding this new threat is essential.
A recent study found a 60% increase in AI-driven phishing attacks. This stark increase highlights the growing danger of phishing. Here's how AI is enhancing phishing and how you can protect yourself.
The Evolution of Phishing
Phishing started simply. Attackers sent mass emails, hoping someone would fall for the bait. These emails often had poor grammar and contained obvious lies. Many people could easily spot these scams.
However, times have changed. Attackers now use AI to refine their techniques. AI helps them craft convincing messages and target specific individuals, making phishing more effective.
How AI Enhances Phishing
Creating Realistic Messages
AI can analyze vast amounts of data to understand how people communicate. This enables it to create realistic phishing messages that mimic the tone and style of legitimate communications, making them harder to identify.
Personalized Attacks
AI can gather information from social media and other sources to create personalized messages. These messages might reference your job, hobbies, or recent activities, increasing the likelihood that you'll believe they're genuine.
Spear Phishing
Spear phishing targets specific individuals or organizations and is more sophisticated than regular phishing. AI makes spear phishing even more dangerous by helping attackers research their targets in depth, allowing them to craft highly tailored messages.
Automated Phishing
AI automates many aspects of phishing. It can quickly send out thousands of phishing messages and adapt them based on responses. If someone clicks a link but doesn't enter information, AI can send a follow-up email, increasing the chances of success.
Deepfake Technology
Deepfakes use AI to create realistic fake videos and audio. Attackers can use deepfakes in phishing attacks, such as creating a video of a CEO requesting sensitive information, adding a new layer of deception.
The Impact of AI-Enhanced Phishing
Increased Success Rates
AI makes phishing more effective, leading to more data breaches. Companies lose money, and individuals face identity theft and other issues.
Harder to Detect
Traditional phishing detection methods struggle against AI-enhanced attacks. Spam filters may not catch them, and employees may not recognize them as threats, making it easier for attackers to succeed.
Greater Damage
AI-enhanced phishing can cause significant damage. Personalized attacks can lead to major data breaches, giving attackers access to sensitive information and disrupting operations.
How to Protect Yourself
Be Skeptical
Always be skeptical of unsolicited messages, even if they appear to come from a trusted source. Verify the sender's identity and avoid clicking on links or downloading attachments from unknown sources.
Check for Red Flags
Look for red flags in emails, such as generic greetings, urgent language, or requests for sensitive information. Be cautious if the email seems too good to be true.
Use Multi-Factor Authentication (MFA)
MFA adds an extra layer of security. Even if an attacker gets your password, they'll need another form of verification, making it harder to access your accounts.
Educate Yourself and Others
Education is key. Learn about phishing tactics and stay informed about the latest threats. Share this knowledge with others, as training can help people recognize and avoid phishing attacks.
Verify Requests for Sensitive Information
Never provide sensitive information via email. If you receive a request, verify it through a separate communication channel, such as contacting the person directly using a known phone number or email address.
Use Advanced Security Tools
Invest in advanced security tools. Anti-phishing software can help detect and block phishing attempts, while email filters can screen out suspicious messages. Keep your security software up to date.
Report Phishing Attempts
Report phishing attempts to your IT team or email provider. This helps them improve their security measures and protects others from similar attacks.
Enable Email Authentication Protocols
Email authentication protocols like SPF, DKIM, and DMARC help protect against email spoofing. Ensure these protocols are enabled for your domain to add an extra layer of security to your emails.
Regular Security Audits
Conduct regular security audits to identify vulnerabilities in your systems. Addressing these vulnerabilities can help prevent phishing attacks.
Need Help with Safeguards Against Phishing 2.0?
Phishing 2.0 is a serious threat. AI amplifies the danger, making attacks more convincing and harder to detect. Have you had an email security review lately? Maybe it’s time.
Frequently Asked Questions
What are the benefits of cybersecurity services?
Cybersecurity services offer numerous advantages for businesses. They protect your sensitive data from unauthorized access, safeguard your systems from cyber threats, ensure compliance with industry regulations, and enhance the overall resilience of your IT infrastructure.
What are managed IT service providers?
Managed IT service providers handle your IT needs, allowing you to focus on your core business operations. They provide proactive IT support, network monitoring, data backup, cybersecurity, and other essential services to ensure the smooth functioning of your IT environment.
What are IT security services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include but are not limited to network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
What makes our IT Support different from other MSPs?
At Inman Technologies, we stand out as a premier outsourced IT support provider in Fort Worth through our unique approach to technology services. Unlike other providers, we don't believe in one-size-fits-all solutions or long-term contracts that lock you in. Instead, we offer:
✔️ Flexible Service Model
✔️ Comprehensive Support
✔️ Innovation Focus - AI-powered solutions
✔️ Local Expertise
Whether you're a small tax office or a growing enterprise, our outsourced IT support services provide the flexibility, expertise, and personal attention your business needs to thrive in today's digital landscape.
📅 Schedule an Appointment With Us to learn more about our unique approach to IT support.
Share Your IT Burdens With Us
Spend less time on IT problems and more time growing your business. Let’s get to know each other and determine how our partnership could grow. With us on your side, develop customized security plans, stronger communication strategies, and a better plan for the future.
Click the button below to schedule your appointment. We’re ready to jumpstart your IT journey.












