Business Outcomes Powered by IT
Fort Worth Outsourced IT Support & IT Services
Let our team at Inman Technologies provide you with the best IT support and solutions to increase your profitability and allow you to focus on growing your business.
Your Neighborhood IT Department
Why Choose Us
We Listen
We take a genuine approach to best understand your business by listening to your needs and simplifying the entire experience.
We Discover
We do a deeper dive into your current processes, network, and infrastructure to identify strengths, weaknesses, and overall IT needs.
We Recommend
We take our findings from the assessments and recommend an IT approach that will best support your business needs and goals.
We Improve
We keep your technology environment constantly improving as needed to help you maintain a competitive edge in your industry.
Client Success Stories

"I have had the good fortune to work with Inman Technologies for the past two years where they have managed and supported a full range of IT services from basic computer setup and software management to a complete overhaul or our servers and security protocols.
Above all, we have developed a relationship with Sean and his team due to their thoroughness and quick response to all our needs."
Bobby Snyder, President of Construction
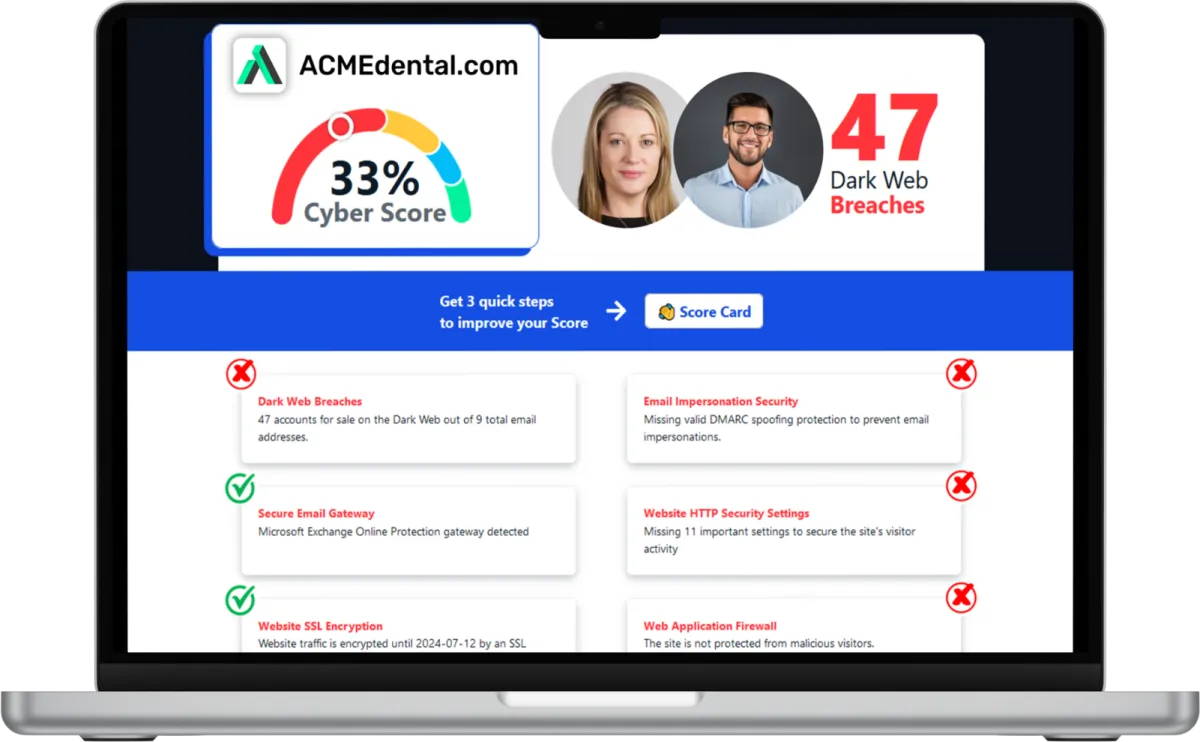
Want to see your Score? Get it in 30 seconds!
If You’ve Been Dealing with IT Challenges,
You’re Not Alone

Sean Inman
Founder & CEO
Inman Technologies is Here to Help.
Inman Technologies is a leading managed IT service provider in Fort Worth, TX, offering a comprehensive selection of outsourced IT support and IT services to businesses in Fort Worth, TX, and the surrounding areas, including Aledo, Willow Park, Hudson Oaks, and Weatherford, TX, and Oklahoma City and Edmond, OK. We specialize in providing IT support and Cybersecurity services to meet the unique needs of businesses.
Call 682-882-9344 today for comprehensive cybersecurity and managed IT services tailored to your needs.
Schedule an Appointment Today
Our Services
We monitor, maintain and manage your IT systems around-the-clock so you can focus on growing your business.
We provide robust protection against cyber threats, ensuring the confidentiality, integrity and availability of your data.
We offer assistance with any sort of IT project - ensuring it's completed on time and on budget.
Harness the Power of AI for Your Business
At Inman Technologies, we bring cutting-edge AI solutions to businesses of all sizes. Our AI as a Service offerings are designed to simplify your operations, enhance customer experiences, and drive measurable growth. From automating customer interactions to optimizing your marketing strategies, we deliver secure, tailored AI tools that make your business smarter and more efficient.
What Clients Say About Us
Partners and products we support to deliver unparalleled productivity:
Business Technology Insights
Explore expert insights, trends, and expert advice on the ever-evolving landscape of information technology. Dive in to discover how we leverage cutting-edge solutions to empower businesses and drive innovation.

9 Signs That Your Smart Home Device Has Been Hacked
Smart home devices are becoming more popular and convenient. But they also pose some serious security risks.

5 Cybersecurity Predictions for 2024 You Should Plan For
Cybersecurity is a constantly evolving field. There are new threats, technologies, and opportunities emerging every year.

Workspaces, a VPN & More – Learn the Newest Microsoft ...
Microsoft Edge continues to redefine user experiences. This is due to Microsoft’s commitment to innovation.

The Costliest Cyber Fails in History
Cyber disasters don’t start with genius hackers in hoodies.
They usually start with something simple. A missed update. A gullible click. A tiny configuration mistake no one double-checked.
Then they explode ... taking down hospitals, shipping companies, and billion-dollar brands.
The difference between a close call and a catastrophe? How well you protect yourself before anything happens.
Here are three of the worst real-world cyber fails… and how we make sure they never happen to you.
1. The Ransomware Nightmare
WannaCry didn’t just make the news ... it made history.
This ransomware wave locked people out of their own data and demanded Bitcoin to get it back. Hospitals couldn’t treat patients. Businesses froze. Governments scrambled.
Why? Because thousands of systems were running unpatched versions of Windows ... with a vulnerability Microsoft had already fixed months before.
How it could’ve been stopped:
Update. Your. Systems.
Patching schedules and automated updates prevent 99% of known vulnerabilities from being exploited.
What we do differently:
Every system we manage gets patched and updated regularly, without relying on someone “remembering.” We also monitor in real time for suspicious activity ... so even if something slips through, it doesn’t get far.
2. The Phishing Trap
One global shipping company learned the hard way that employees are the easiest way into a network.
Attackers sent fake emails that looked like they came from trusted partners. People clicked. They entered credentials. Hackers walked right in.
Without multi-factor authentication (MFA), it was game over. The breach cost millions and shut down operations for weeks.
How it could’ve been stopped:
Train your people to recognize bad emails.
Use MFA so stolen passwords aren’t enough to break in.
What we do differently:
We train employees regularly ... and test them ... so they’re ready for real-world tricks. We also enforce MFA across critical systems so credentials alone won’t open the door.
3. The Cloud Misconfiguration Mess
One social media giant left a massive storage bucket wide open to the public internet. Anyone with the right link could see sensitive data.
It wasn’t a “hack.” It was a bad setting no one noticed.
How it could’ve been stopped:
Run regular cloud security audits.
Enforce access controls so only authorized users can touch sensitive data.
What we do differently:
We audit cloud configurations regularly and lock down permissions so nothing gets exposed. Access is on a need-to-know basis ... and we verify it stays that way.
Your Cyber Protection Checklist
The best time to deal with a cyber threat is before it happens. Here’s what’s non-negotiable:
Regular System Updates & Patches — No excuses.
Ongoing Employee Training — People are your first line of defense.
Multi-Factor Authentication — Stop stolen credentials from becoming full-blown breaches.
Cloud Security Audits — Catch mistakes before the bad guys do.
24/7 Monitoring — Threats don’t clock out at 5 p.m., and neither do we.
Bottom line: Cyber disasters don’t announce themselves. They hit fast, cost big, and often start with something that could have been fixed in minutes.
If you’re already a client, you can breathe easy ... we’ve got your bases covered. If you’re not, don’t wait until your name is in the next headline. Let’s lock things down now.
Frequently Asked Questions
What are the benefits of cybersecurity services?
Cybersecurity services offer numerous advantages for businesses. They protect your sensitive data from unauthorized access, safeguard your systems from cyber threats, ensure compliance with industry regulations, and enhance the overall resilience of your IT infrastructure.
What are managed IT service providers?
Managed IT service providers handle your IT needs, allowing you to focus on your core business operations. They provide proactive IT support, network monitoring, data backup, cybersecurity, and other essential services to ensure the smooth functioning of your IT environment.
What are IT security services?
IT security services encompass measures and practices to protect your systems, networks, and data from potential threats. These services include but are not limited to network security, data encryption, access controls, vulnerability assessments, penetration testing, and incident response.
What makes our IT Support different from other MSPs?
At Inman Technologies, we stand out as a premier outsourced IT support provider in Fort Worth through our unique approach to technology services. Unlike other providers, we don't believe in one-size-fits-all solutions or long-term contracts that lock you in. Instead, we offer:
✔️ Flexible Service Model
✔️ Comprehensive Support
✔️ Innovation Focus - AI-powered solutions
✔️ Local Expertise
Whether you're a small tax office or a growing enterprise, our outsourced IT support services provide the flexibility, expertise, and personal attention your business needs to thrive in today's digital landscape.
📅 Schedule an Appointment With Us to learn more about our unique approach to IT support.
Share Your IT Burdens With Us
Spend less time on IT problems and more time growing your business. Let’s get to know each other and determine how our partnership could grow. With us on your side, develop customized security plans, stronger communication strategies, and a better plan for the future.
Click the button below to schedule your appointment. We’re ready to jumpstart your IT journey.























